在Switch上的設定
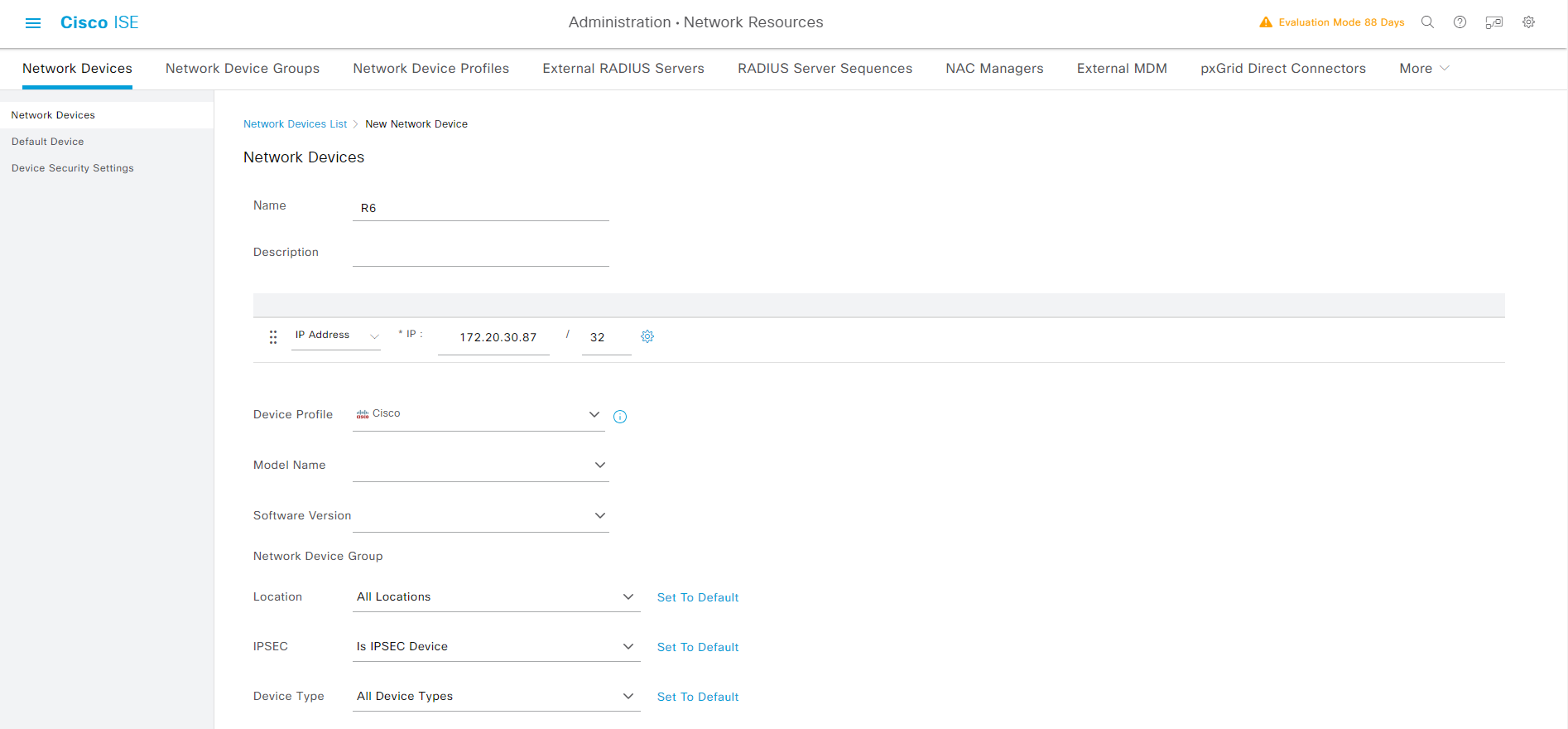
hostname R6
enable algorithm-type scrypt secret {Password}
ip domain name abc.com
username admin algorithm-type scrypt secret {Password}
line vty 0 4
login local
transport input ssh
crypto key generate rsa
aaa new-model
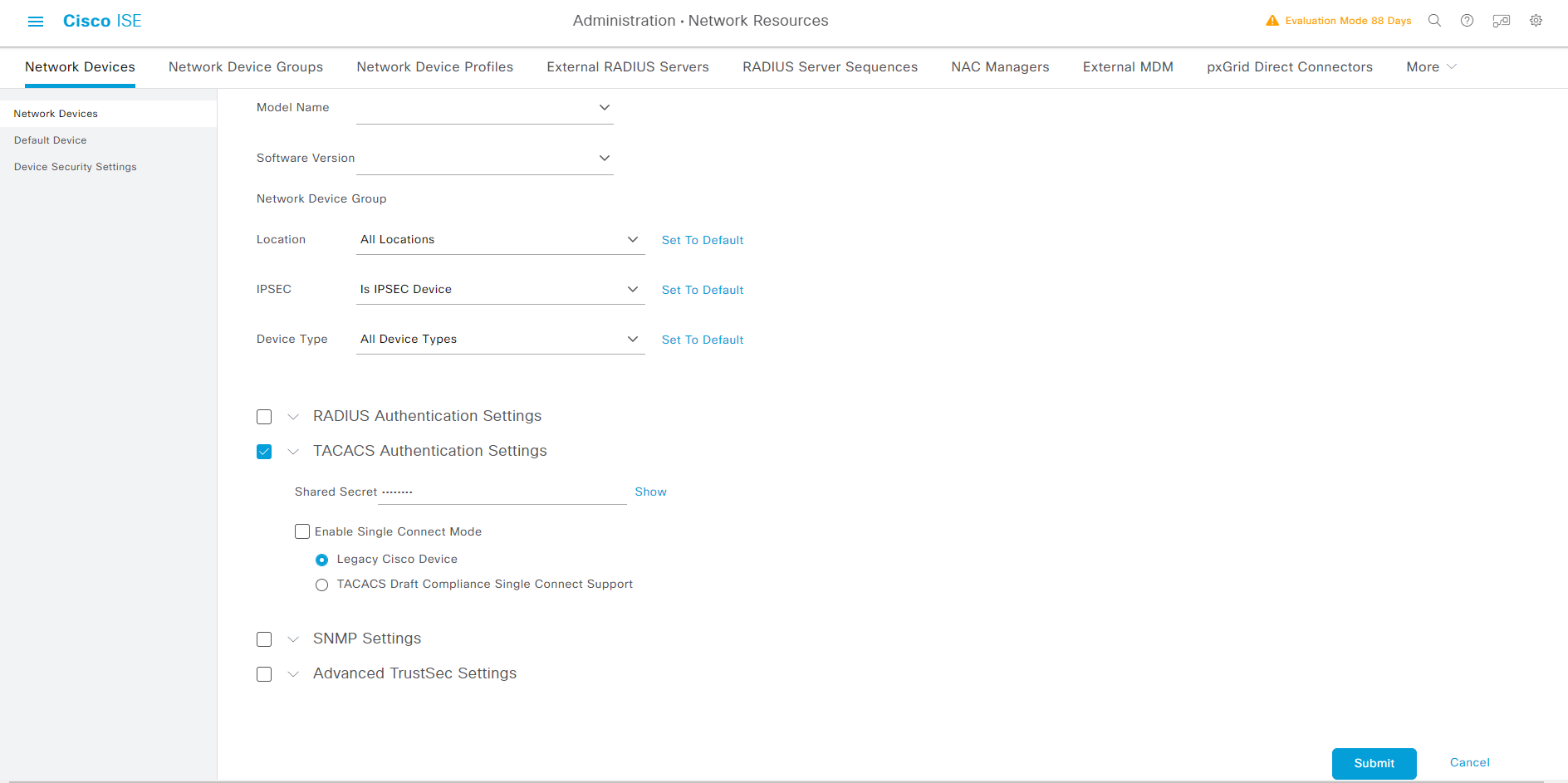
tacacs-server host {ISE IP} key {Password}
設定好以上的設定就可以測試驗証
test aaa group tacacs+ {ID} {Password} new-code
正常的話會看到success, 但是還未能使用, 還要設定下面真正驗証的時候使用tacacs+, 下面的設定可以等ISE設好之後再設定
aaa authentication login default group tacacs+ local
aaa authorization exec default group tacacs+ local
aaa accounting exec default start-stop group tacacs+
打開ISE
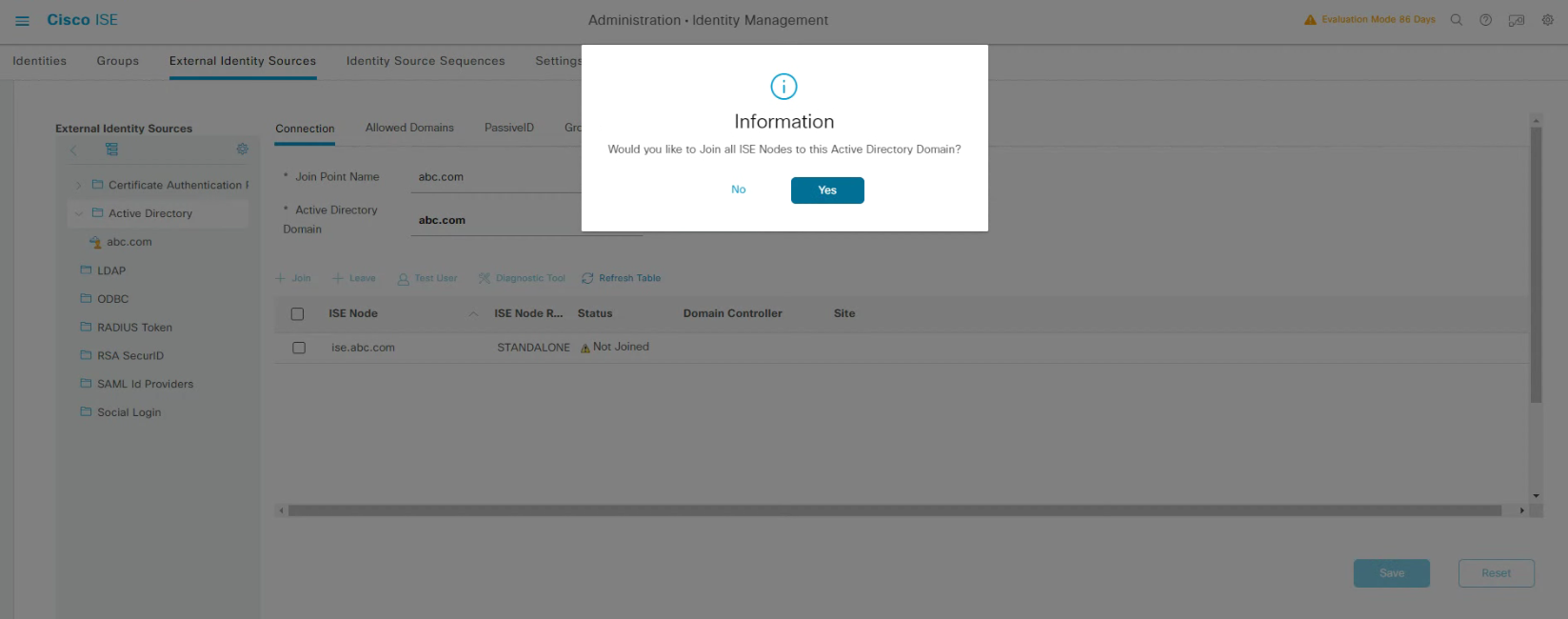
Administration -> Identity Management -> External Identity Sources -> Active Directory -> Add
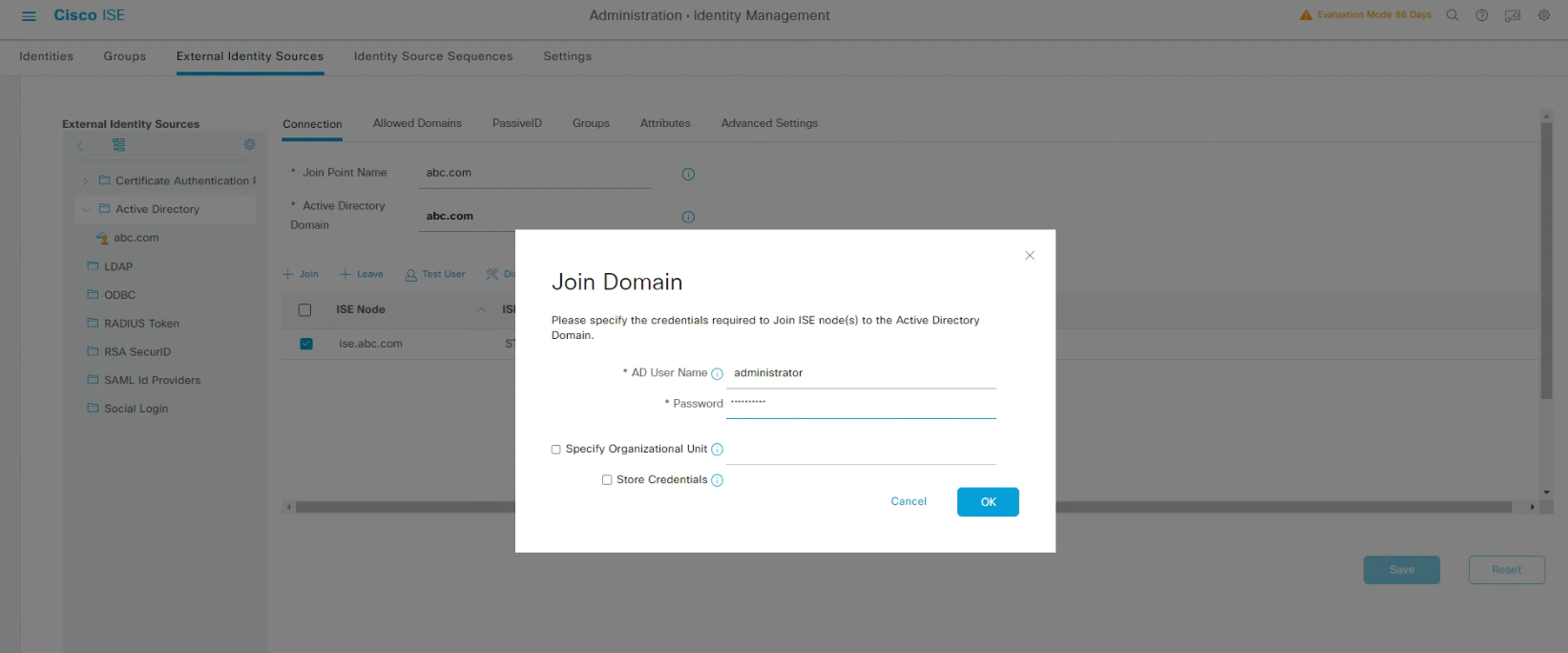
輸入AD domain
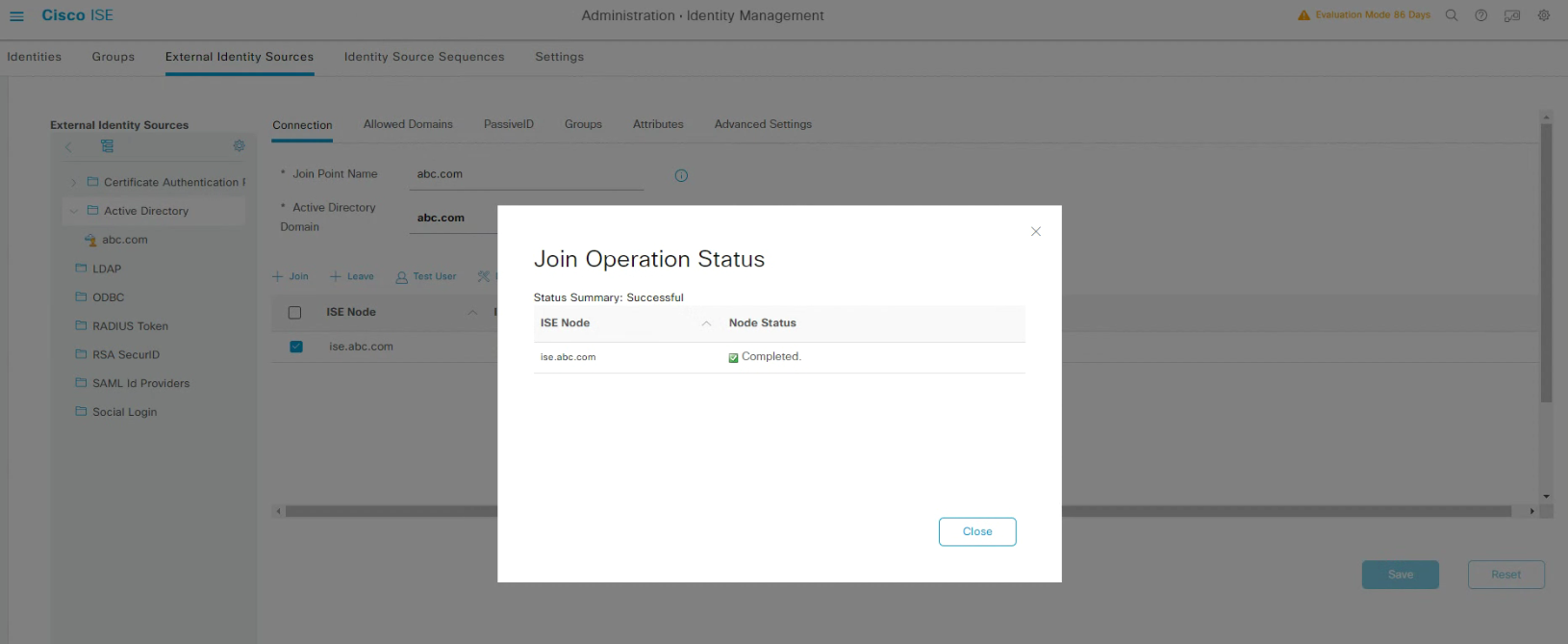
然後就會看到Completed
然後再增加相對的Devices
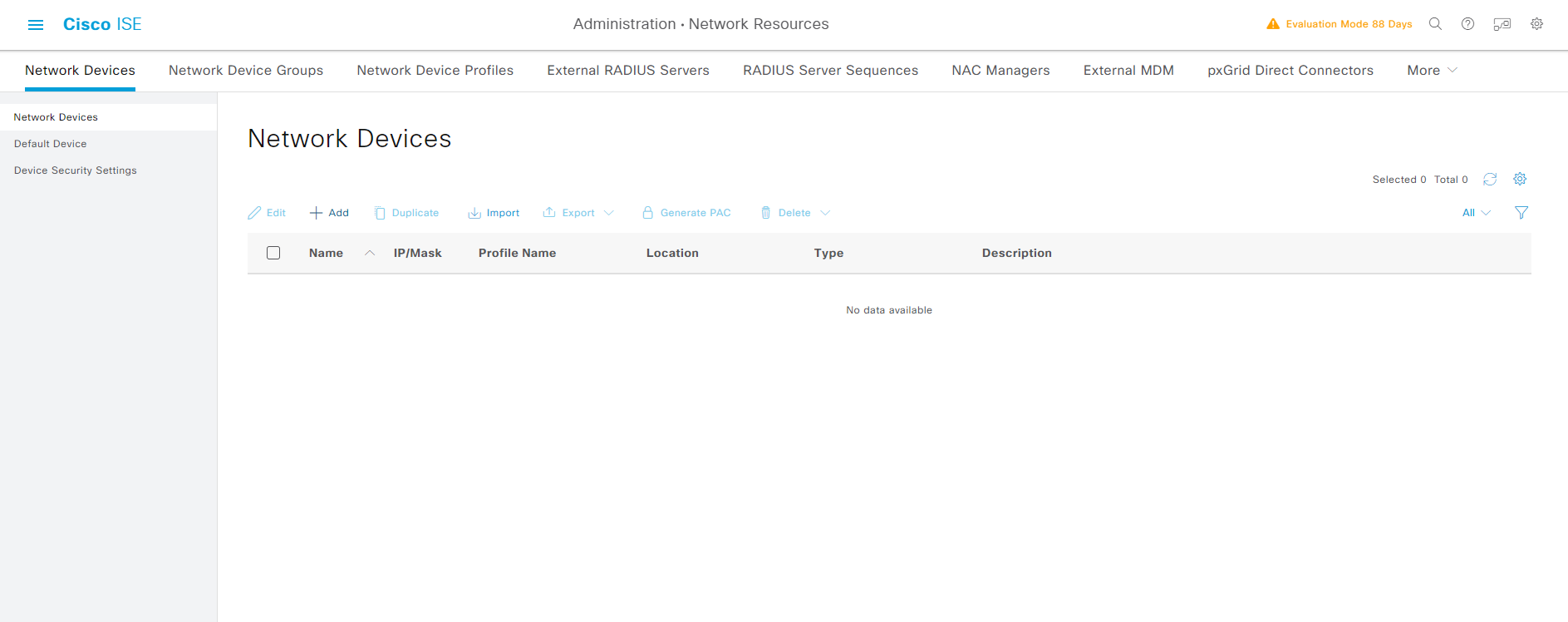
Administration -> Network Resources -> Network Devices -> Add
然後到可以登入的使用者
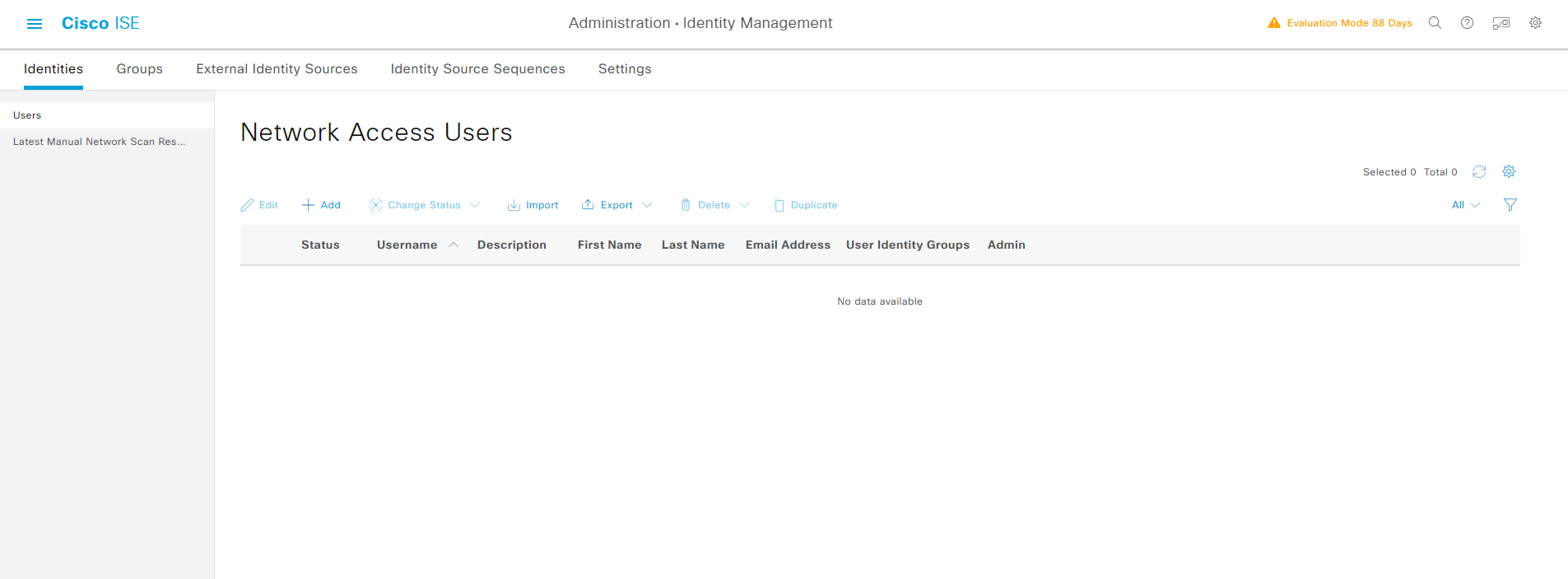
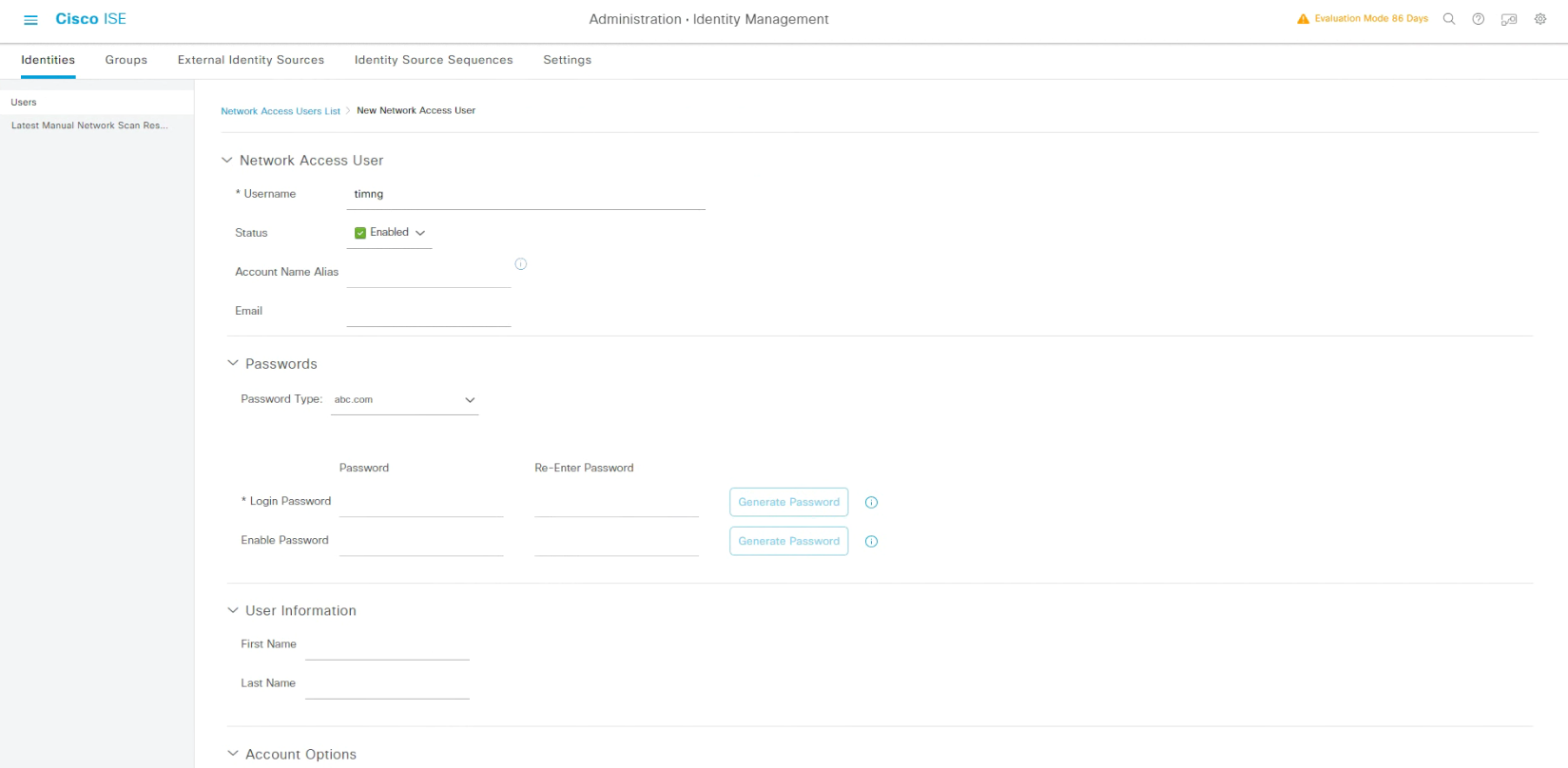
Administration -> Identity Management -> Identities -> Users -> Add
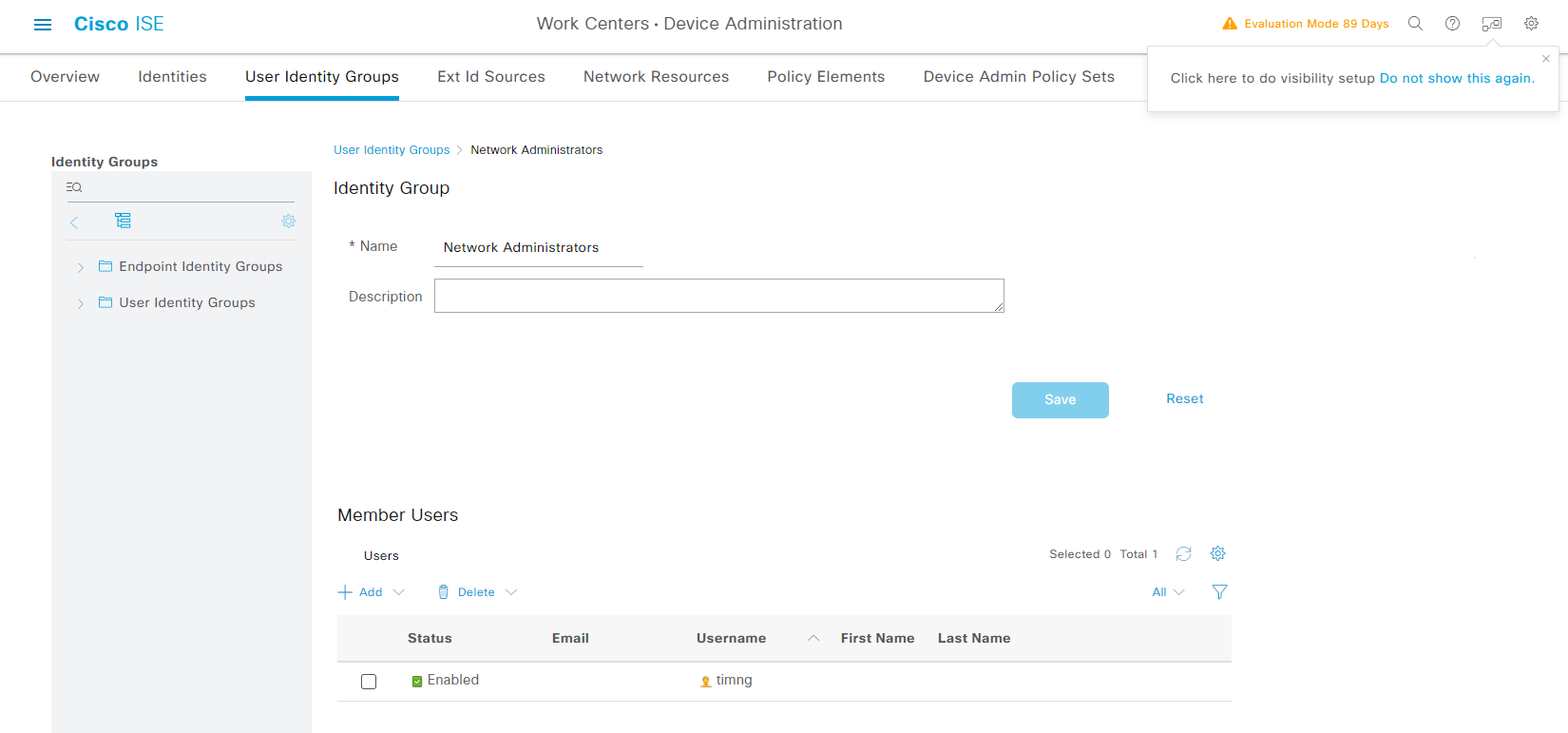
建立一個Network Administrators Group
Work Centers -> Device Administration -> User Identity Groups -> Add
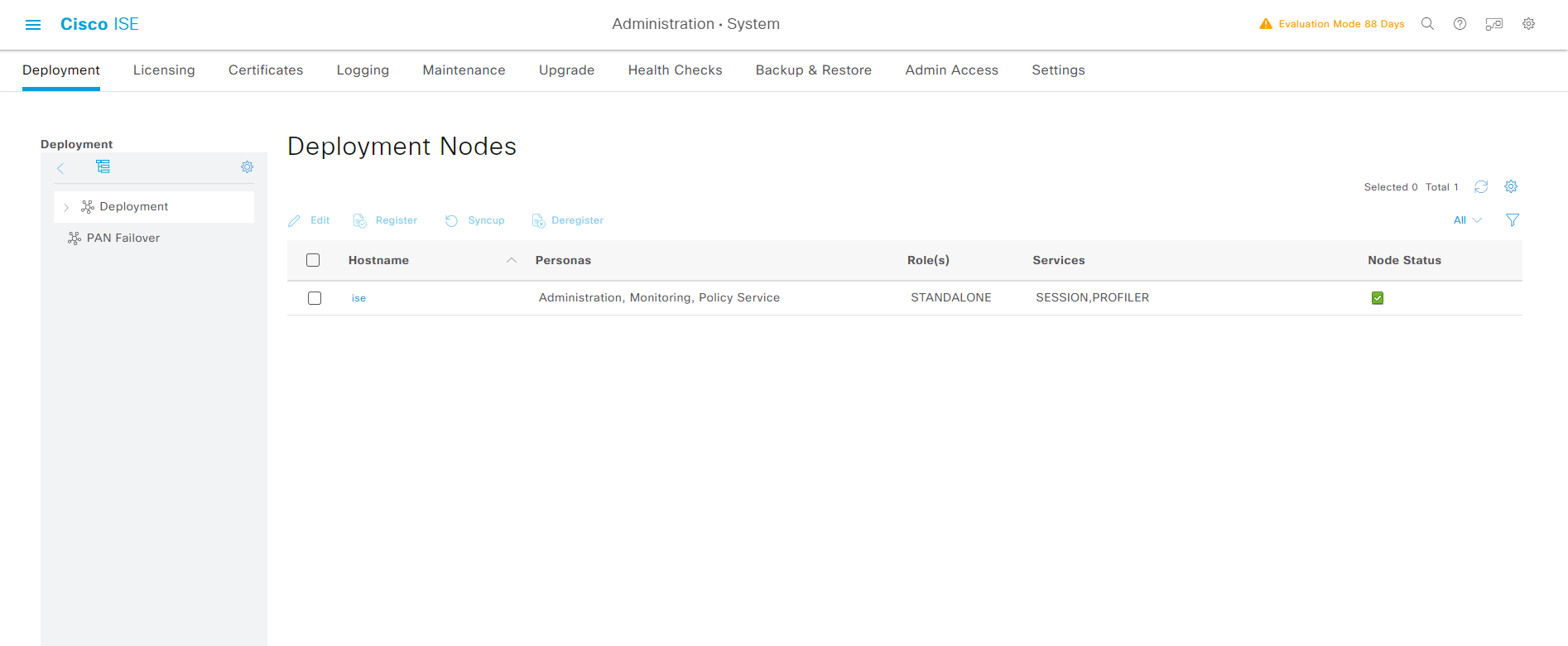
Administration -> System -> Deployment -> Deployment Nodes
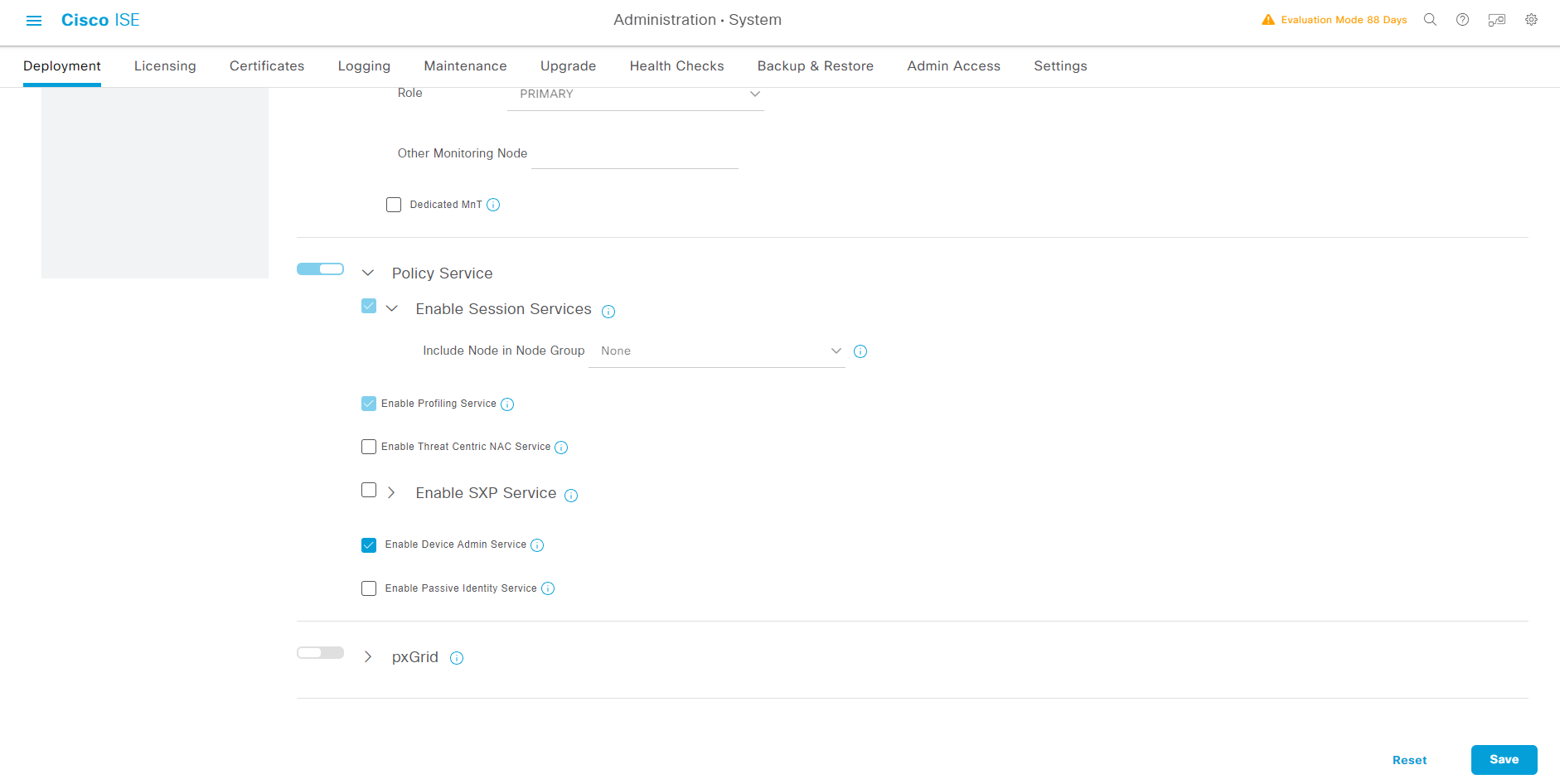
Enable "Enable Device Admin Service"
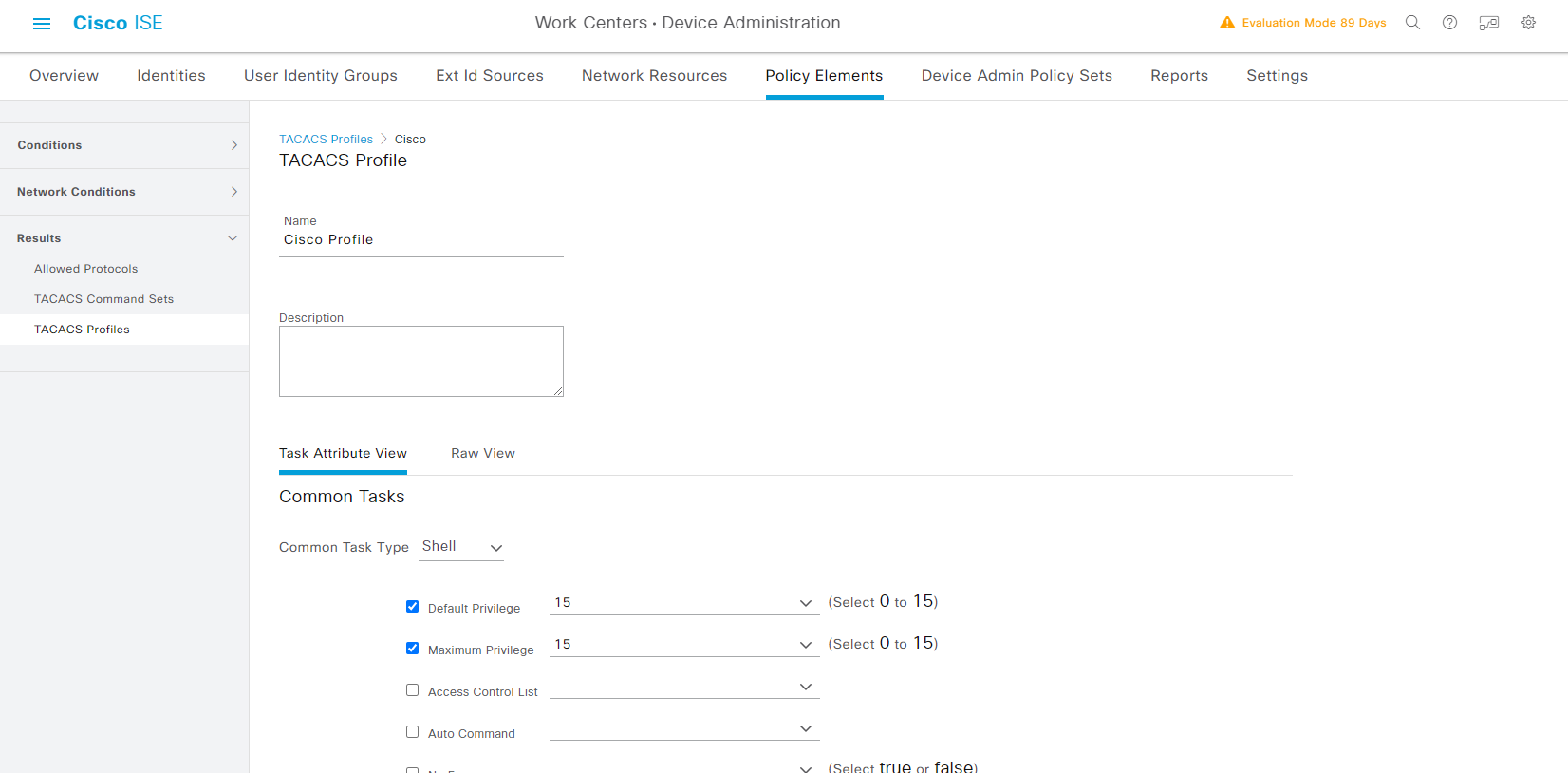
建立Profile之前先定義好Shell & Profile
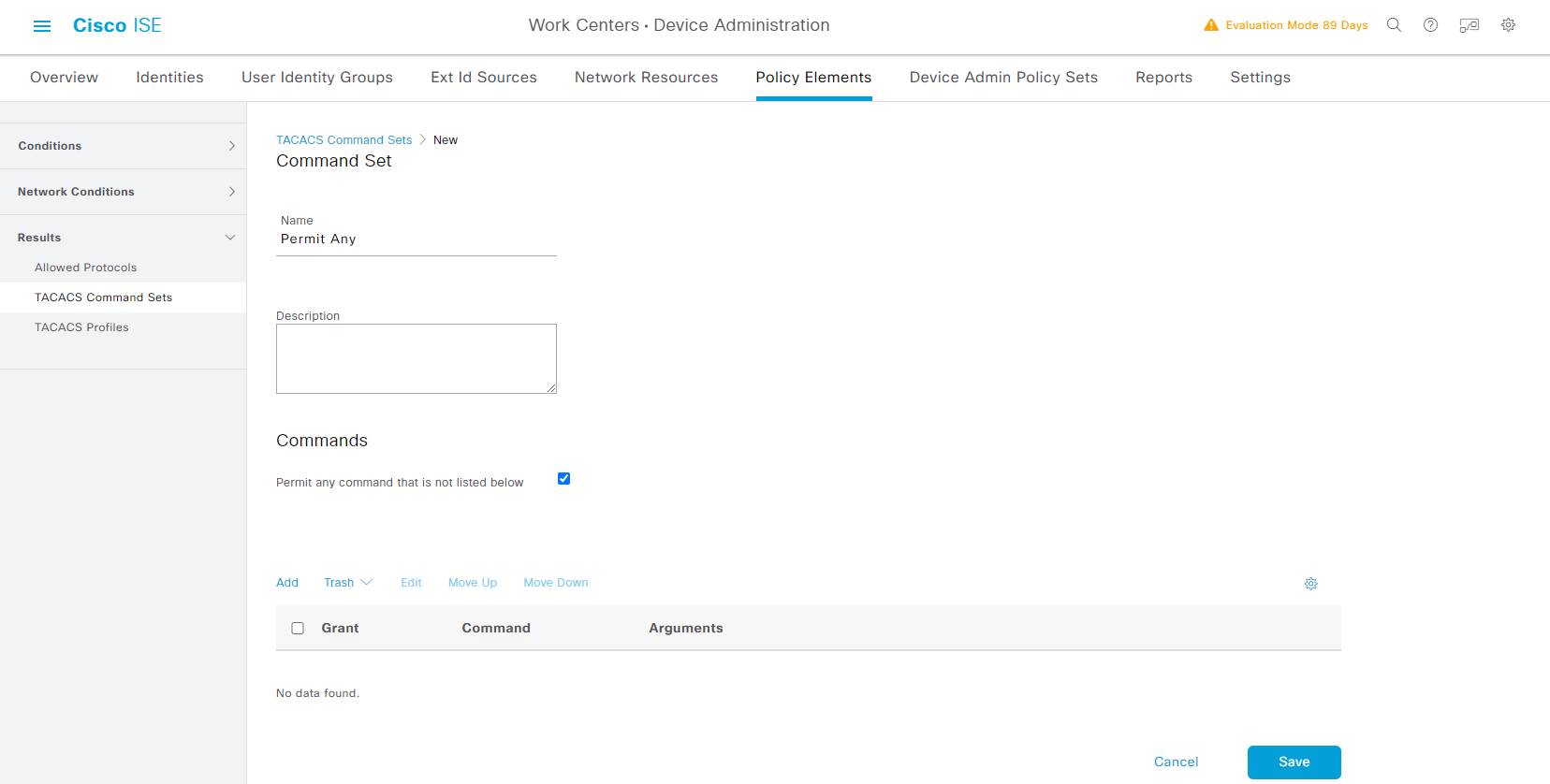
Work Centers -> Device Administration -> Policy Elements -> Results -> TACACS Command Sets
Work Centers -> Device Administration -> Policy Elements -> Results -> TACACS Profiles
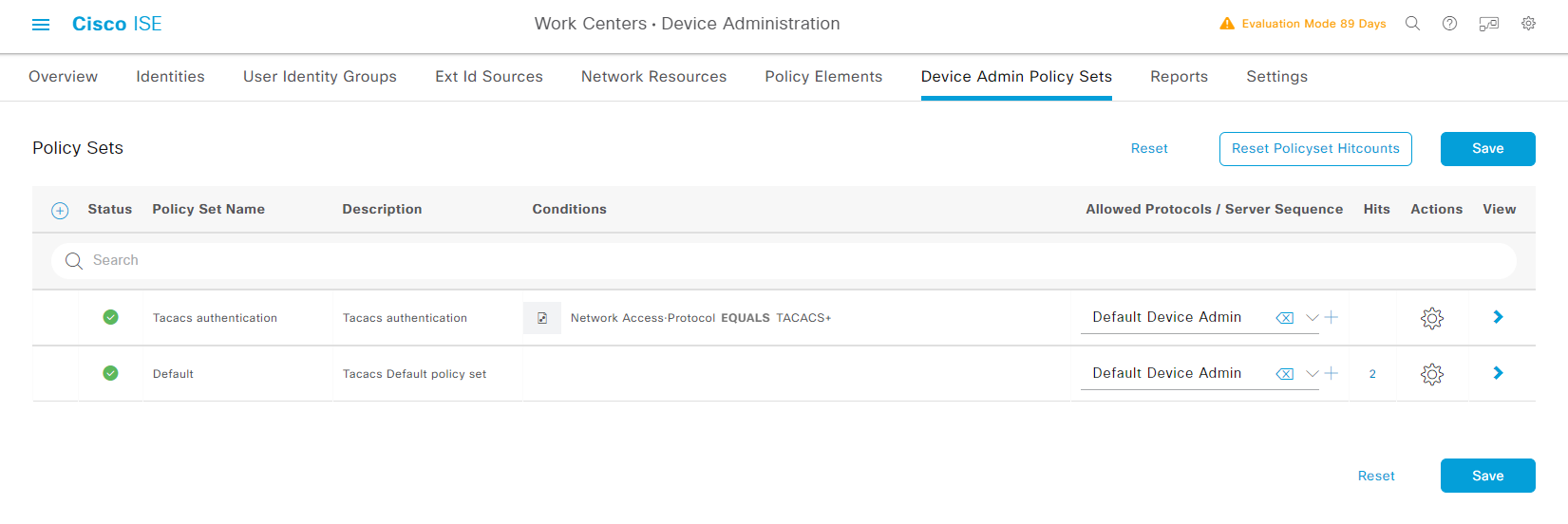
 Work Centers -> Device Administration -> Device Admin Policy Sets -> Policy Sets
Work Centers -> Device Administration -> Device Admin Policy Sets -> Policy Sets
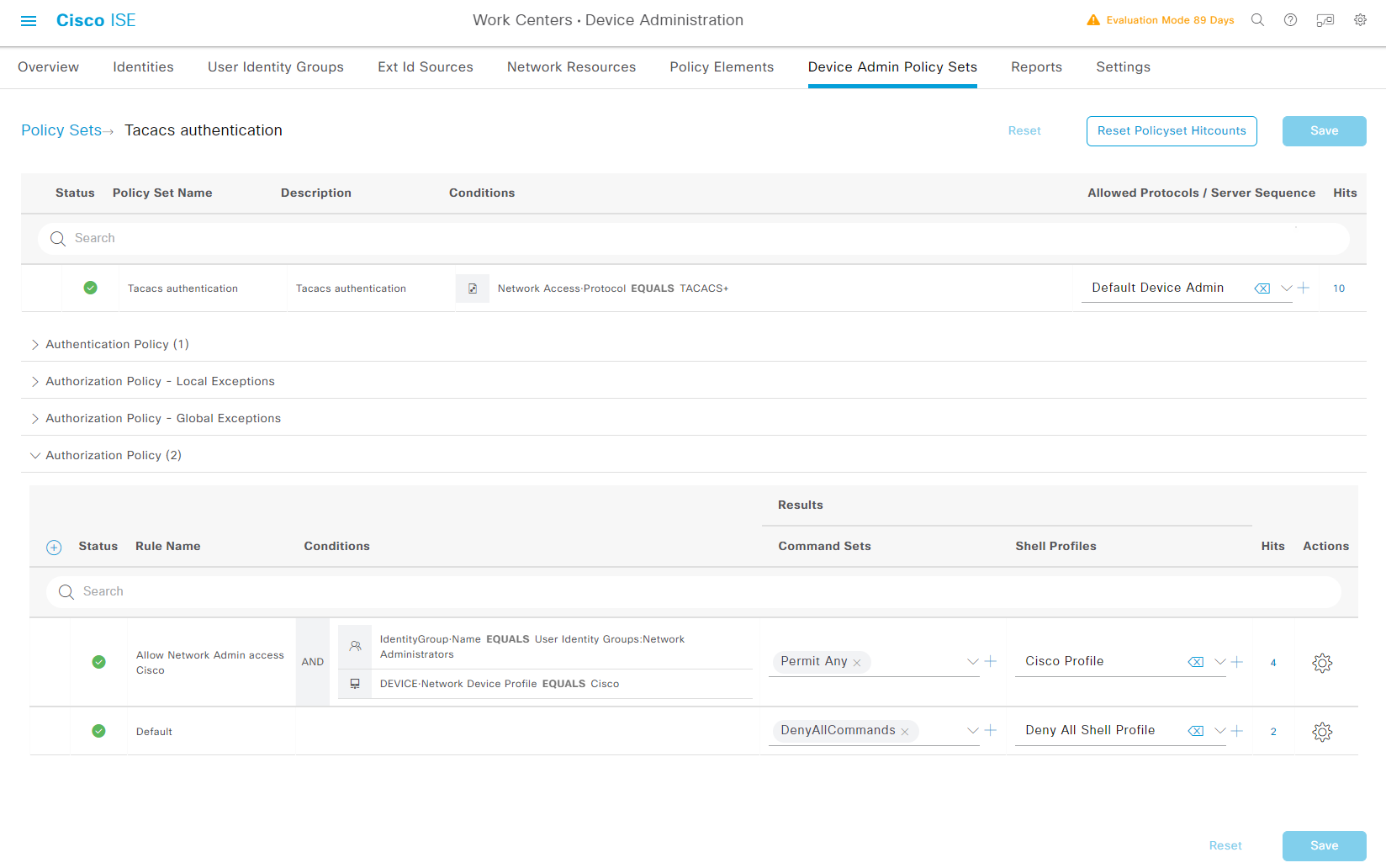
建立一個新的Policy
Authentication Policy可以留待更覆習的情怳再更改, 現在主要看Authorization Policy, 在這裏設定一個Conditions, 如果是我們之前定義的Network Administrators而且是Cisco Devices的話, 就Permit